NIST CSF 2.0 Score Converter | Why Your Organisation Should Be Transitioning

TL;DR
Want to skip forward and know how your organisation stacks up against the updated framework? We have created a NIST 1.1 to 2.0 Converter Tool that will take existing NIST CSF 1.1 scores and convert them into NIST CSF 2.0 scores.
If you’d like further help in your transition to NIST 2.0, contact us.
Summary
NIST Cybersecurity Framework (CSF) 2.0 will support organisations that are having difficulties grappling the complexities of identifying, managing cyber threats, protecting assets, as well as responding and recovering from incidents.
This blog post will cover key updates addressing some of the NIST 1.1 shortfalls, why organisations should transition and key considerations when adopting CSF 2.0.
A broader spectrum and adoption for all
The adoption of NIST CSF 1.1 by various organisations outside of the US critical infrastructure highlights its effectiveness in creating a shared language for managing cyber security risks.
However, NIST CSF 1.1 also had some limitations in its design and adoption:
- Complexity for small businesses: Although CSF 1.1 is designed to be scalable, its complexity and the broad scope of its guidelines can be overwhelming for small to medium-sized businesses that may not have the resources or expertise to fully implement the framework.
- Disparities in control resolution: While the flexibility of CSF 1.1 is a strength because it allows for broad application, it can also be a weakness. Subcategories often either were very granular and specific (e.g. PR.PT-2: removable media is protected) or very high level (e.g. PR.AC-3: Remote access is managed). As a result, some areas of the framework may have been interpreted by each organisation very differently.
- Changes to technological and threat landscape: Since CSF 1.1 was released in 2018, new types of cyber threats and technology have emerged. Additionally, businesses have become more reliant on software vendors, increasing their exposure to supply chain attacks.
In CSF 2.0, NIST has met these challenges designing the framework with all organisations in mind, regardless of their size, industry they operate in, or their technology stack. This broad applicability is achieved through several key aspects:
- Expanded Core Guidance and Resources: NIST has updated the CSF’s core guidance and developed a suite of resources to assist organisations in achieving their cybersecurity goals.
- Addition of the Govern Function: The inclusion of the “Govern” function in CSF 2.0 emphasises governance and how organisations make and execute informed decisions on cybersecurity strategy. This reflects a broader understanding that cybersecurity is a major source of enterprise risk that needs to be integrated with other organisational priorities, such as regulatory and financial.
In this post, we highlight three key interesting changes in NIST CSF 2.0 that resolve some of the key gaps and limitations in NIST CSF 1.1.
A greater emphasis on Supply Chain management
While CSF 1.1 addressed supply chain management, it lacked the certain specifics of the management lifecycle (e.g., terminating a relationship), especially now that the “digital supply chain” has become a fundamental component of business operations.
Where previously Supply Chain management sits under Identify, now it appropriately sits under the new function “GOVERN”, consisting of ten subcategories. Moving Supply Chain Risk Management under the GOVERN function highlights its importance to the organisation’s leaders.
Of the changes and additions to the Supply Chain category, the following subcategory focuses on a key gap that we observe in a majority of organisations’ supply chain risk processes:
- GV.SC-10: Planning for termination of the relationship.
Offboarding suppliers is key to reducing the risk of data breaches weeks, months or years after a supplier relationship has ended.
GV.SC-10 defines the need to establish offboarding processes to ensure that organisations remove organisational data, access and other dependencies after the conclusion of a third party service or partnership.
Organisations are often focused on the onboarding and ongoing maintenance of cyber security for new and existing suppliers, however, often overlook the processes required to offboard terminated suppliers. This can result in organisations suffering from data breaches weeks, months or even years after they have stopped working with a supplier.
To ensure that organisations reduce their risk of a third party cyber security event impacting them after termination of service, organisations should have offboarding processes that include:
- Removing logical or physical access for any third party personnel after the agreed termination date.
- Requesting evidence of data deletion, ensuring that this also covers any backups of data as well.
- Collecting any physical media or devices provisioned to third party personnel.
Focus on improvement and alignment to risk
While NIST CSF 1.1 did have some subcategories for improving protection processes, these were hidden in larger categories and its importance not emphasised. Moving to CSF 2.0 not only addressed this issue by consolidating into one category under IDENTIFY (ID.IM), but also updated the language. The four subcategories of Improvement are now more descriptive along with the addition of example actions. This should provide organisations with a clearer understanding of what is required to uplift their cybersecurity posture.
We have identified a new subcategory under ID.IM which may implicate substantial effort by any organisation, but equally will yield significant benefits in return:
- ID.IM-01: Improvements are identified from evaluations.
Organisations should regularly reflect their performances on protective processes and identify areas for improvement.
The introduction of the ID.IM category emphasises the importance of testing the effectiveness of controls. In particular, ID.IM-01 requires organisations to perform evaluations of the effectiveness of their security controls to ensure that there is a business process in place that prompts action for improvements.
While many organisations look to performing maturity assessments, this is often not enough to evaluate and identify improvements in cyber security protections.
To meet the intent of this control, organisations should consider:
- Conducting cyber security effectiveness assessments that look at processes, people and tools used to deliver cyber security controls.
- Defining, collecting and assessing metrics and service level objectives of cyber security capabilities to support periodic assessment of cyber security effectiveness.
- Collaborating with trusted external advisors or functionally independent internal parties (e.g. internal audit or risk functions) to test the effectiveness of cyber security capabilities.
In addition to the above, we wanted to mention Oversight (GV.OV) in GOVERNANCE. A distinct difference to ID.IM is that here GV.OV targets the management rather than specific controls, such as:
- GV.OV-02: The cybersecurity risk management strategy is reviewed and adjusted to ensure coverage of organizational requirements and risks.
- GV.OV-03: Organizational cybersecurity risk management performance is evaluated and reviewed for adjustments needed.
We often find that cyber security strategies focus on increase of maturity rather than a reduction of risk. While there are overlaps in these objectives, achievement of maturity can sometimes contradict the goal of risk reduction. This can manifest in the following ways:
- Introduction of control for maturity gain introduces increased user friction resulting in lower productivity and negative impacts costing more than the risk the control is meant to mitigate or;
- Introduction of control does not meet a risk mitigation objective at all.
To ensure that cyber security strategies are aligned to risk mitigation objectives, organisations should:
- Map strategic projects to specific risks that they will buy down.
- Review where security controls or projects impede productivity or innovation beyond the risk mitigation benefit it is meant to provide.
- Periodically review the strategy (we suggest either on an annual basis or on significant change to the organisation, its risks as well as any significant incidents).
Free tools to assist in adopting NIST CSF 2.0
As highlighted before, NIST has broadened the foundational guidance of the framework and introduced additional tools and resources. NIST has introduced the CSF 2.0 Reference Tool, a novel utility aimed at simplifying the adoption of the framework for organisations. This tool enables you to navigate, query, and download information from the CSF’s foundational guidance in both easy-to-understand and technically detailed formats. Complementing this, the Cybersecurity and Privacy Reference Tool (CPRT) from NIST aggregates a comprehensive, interconnected, and downloadable collection of NIST’s guidance documents, including the CSF itself.
Another self-guided tool is the introduction of CSF Organisational Profiles. Organisational Profiles give you the framework to build a current and target state profile using a newly introduced organisational profile template, serving as a starting point to identify the discrepancies required to achieve your targeted cyber maturity level.
Interested in seeing how you stack up against NIST CSF 2.0?
Overall, NIST CSF 2.0 provides significant improvement in clarity and inclusion of new relevant subcategories. As a result, we strongly recommend that organisations transition to NIST 2.0 sooner rather than later to adopt these new inclusions and ultimately bolster their cyber security posture.
While NIST has provided mappings between NIST CSF 1.1 to 2.0, we have gone a step further and built the NIST CSF Transition tool, a maturity converter tool that will allow you to input your NIST CSF 1.1 scores and convert them to NIST CSF 2.0 scores.
Accessing and using the tool
The NIST 1.1 to 2.0 Converter can be downloaded here.
Instructions on how to use the tool
The NIST CSF Transition tool requires just three simply steps:
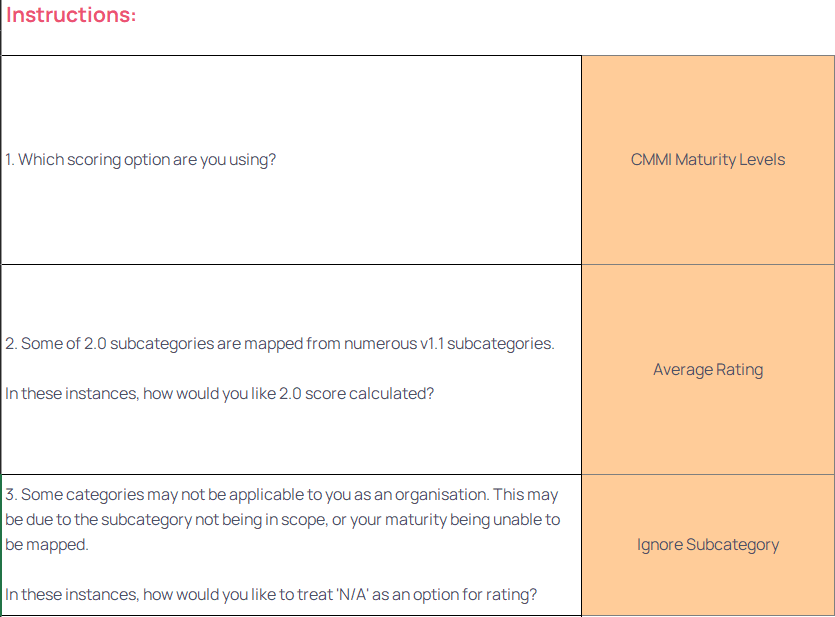
Choosing Scoring, Calculation, and N/A Treatment Option: Select how scores should be calculated based on your organisation’s specific context.
There are three selectors on the ‘Start Here’ tab, shown below, with the following options:
Input current NIST CSF 1.1 subcategory scores: Enter your existing scores in the ‘NIST CSF 1.1’ tab, shown below, either using CMMI Maturity Levels (0-5) or NIST CSF Implementation Tiers (1-4).
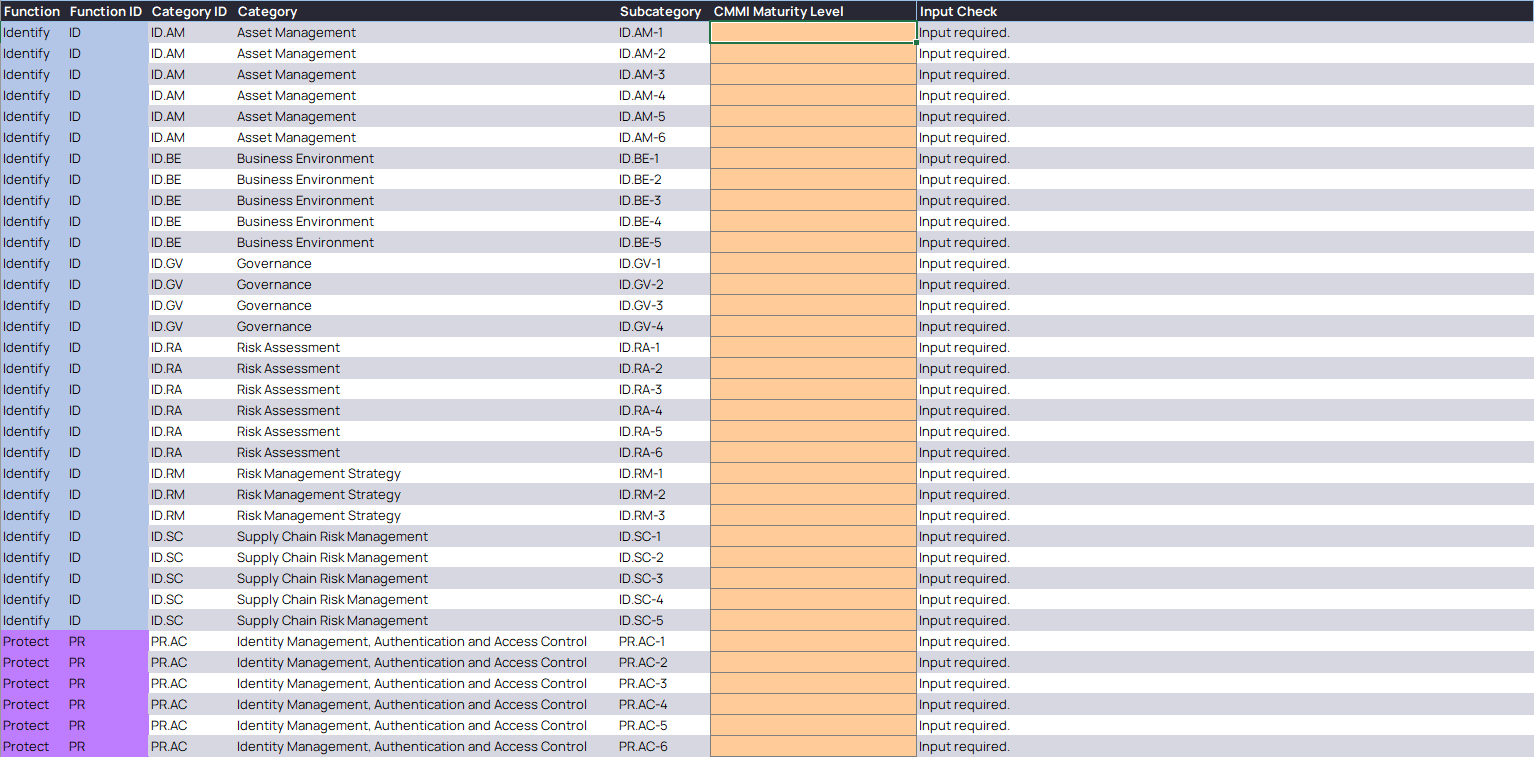
Enter your current 1.1 scores on the NIST CSF 1.1 tab [Optional] Define scores for the newly introduced NIST CSF 2.0 subcategories: Enhance your understanding of current maturity by scoring the subcategories introduced with the release of version 2.0 of the framework.
This optional step adds context and completeness to your current state maturity. The 16 new subcategories’ input on the ‘Unmapped 2.0 Subcategories’ tab, shown below, is restricted to dropdowns of whole numbers, based on which Scoring Option is selected, as well as ‘N/A’.
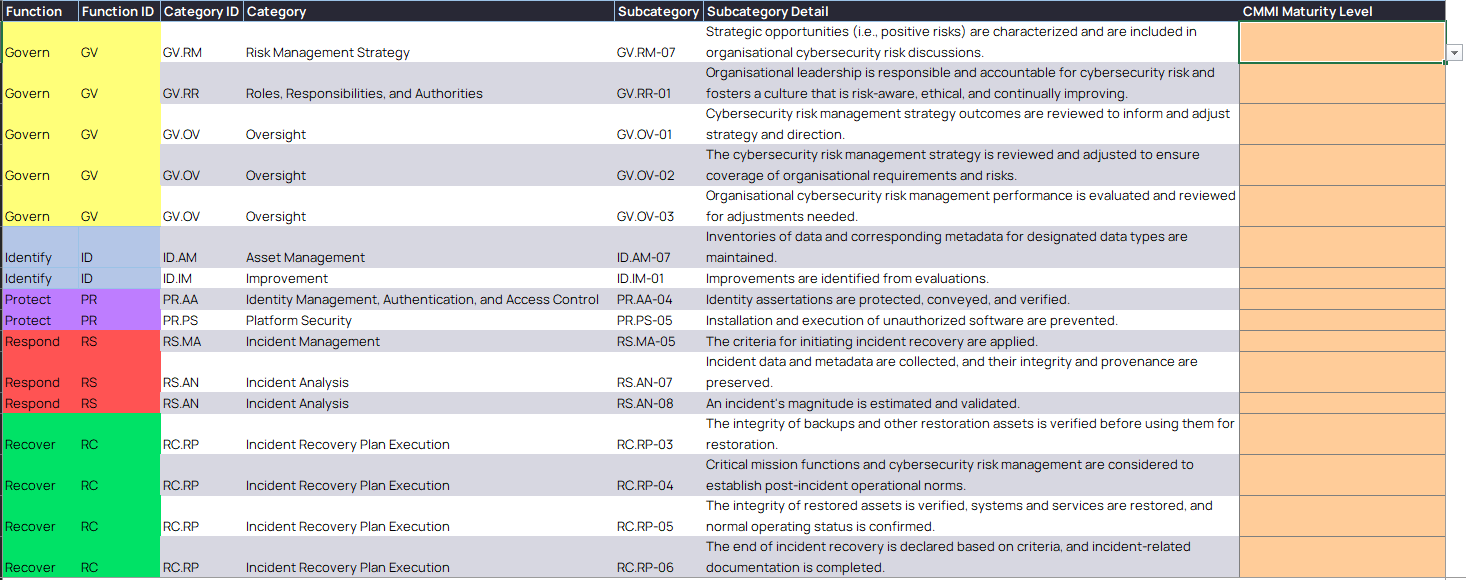
Enter scores of the new subcategories on the Unmapped 2.0 Subcategories tab
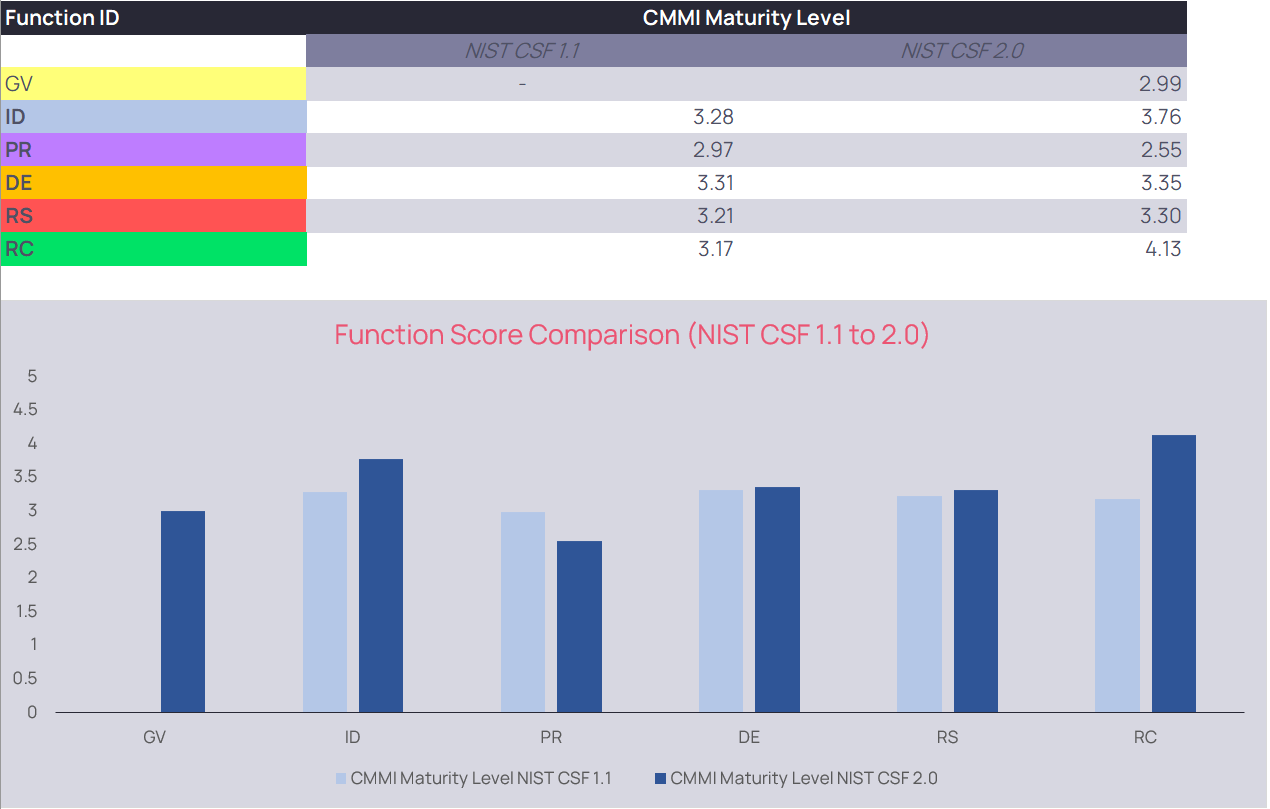
And that’s it! Now you can go through the Summary and NIST 2.0 tabs to see how your current maturity stacks up. The tool provides breakdowns across framework version, function, category, and subcategory to allow organisations to identify where they may want to focus their uplift effort.
The following screenshots highlight example outputs based on dummy NIST CSF 1.1 scores.
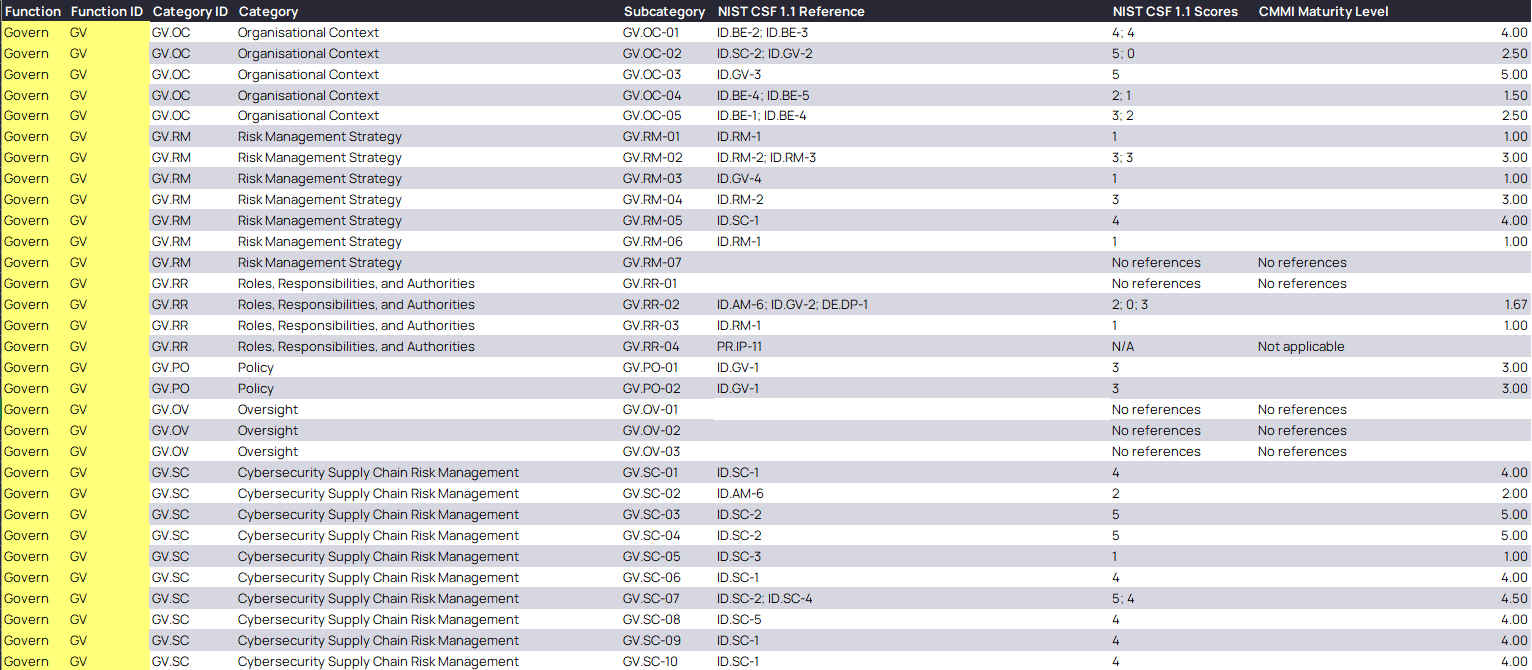
Worked example
Let’s explore how 2.0 scores change based on the dropdowns selected. Consider the subcategory GV.RR-02 from 2.0 of the framework. This subcategory maps to the following 1.1 subcategories, along with their assumed scores for this exercise:
- ID.AM-6 = ‘2’
- ID.GV-2 = ‘4’
- DE.DP-1 = ‘N/A’
Based on the above setup, the following outcomes are possible:
| Scoring Option | Calculation Option | N/A Treatment Option | How it’s calculated | GV.RR-02 Resulting Score |
|---|---|---|---|---|
| CMMI Maturity Levels | Average Rating | Ignore Subcategory | (ID.AM-6 + ID.GV-2 )/ 2 = (2 + 4) / 2 = 3 | 3 |
| Assume Lowest Rating | (ID.AM-6 + ID.GV-2 + DE.DP-1)/ 3 = (2 + 4 + 0) / 3 = 2 | 2 | ||
| Lowest Rating | Ignore Subcategory | ID.AM-6 = 2 | 2 | |
| Assume Lowest Rating | DE.DP-1 = ‘N/A’ = 0 | 0 | ||
| NIST CSF Implementation Tiers | Average Rating | Ignore Subcategory | (ID.AM-6 + ID.GV-2 )/ 2 = (2 + 4) / 2 = 3 | 3 |
| Assume Lowest Rating | (ID.AM-6 + ID.GV-2 + DE.DP-1)/ 3 = (2 + 4 + 1) / 3 = 2.33 | 2.33 | ||
| Lowest Rating | Ignore Subcategory | ID.AM-6 = 2 | 2 | |
| Assume Lowest Rating | DE.DP-1 = ‘N/A’ = 1 | 1 |
Disclaimer
Skylight does not recommend using NIST CSF Implementation Tiers or inputting subcategory scores with decimal places… but that’s a story for another time!
Limitations of the tool
While this tool can assist an organisation in gaining an understanding of their current maturity against NIST CSF 2.0, based on their existing state in 1.1, it is essential to recognise its limitations. Here are some key points:
- Not a complete current state assessment: The tool provides valuable insights, but it is not a substitute for a comprehensive current state maturity assessment. While the mapping is provided by NIST, this doesn’t guarantee that every aspect of the 2.0 subcategory is fully represented by the corresponding 1.1 subcategories. Moreover, for subcategories introduced in 2.0 of the framework, where organisations are allowed to score freely, a more thorough evaluation may be necessary.
- Compatibility with Excel versions: This tool has been built and tested on Excel 365 for Windows. It may not work on other versions of Excel, including versions prior to Excel 365, Excel for the web, and Excel for Mac.
Give us feedback
We hope this tool is helpful to your organisation’s ongoing cyber security journey. As this is the first iteration of the tool, we understand there might be room for improvement. Please share your feedback and ideas on how to enhance this tool by reaching out to us as [email protected].
The NIST 1.1 to 2.0 Converter can be downloaded here.