Introducing GoldiLocked: A Free Cyber Risk Scenario Generator

Summary
How do you build a security control library that is pragmatic and relevant to your organisation’s cyber risks?
Organisations often seek out industry best practice cyber security frameworks to give them these answers. However, while industry best practice frameworks and standards are a great starting point, a lot of organisations do not evolve beyond a verbatim use of the framework, shoehorning them into their organisations.
This contrasts with the recommendation of these very frameworks, often clearly stating that a risk-based approach should be used to select and design the appropriate controls. But how do you actually do that?
Introducing GoldiLocked!
Overview
GoldiLocked aims to help security professionals achieve a risk-based approach to security so they can have security that is not too little, not too much, but just right (inspired by the story of Goldilocks and the Three Bears).
GoldiLocked does that by providing a simple way to create cyber risk scenarios aligned with organisational risks. Once those are defined alongside a risk appetite, a set of matching controls to mitigate the risk within appetite can be generated.
Accessing and using the tool
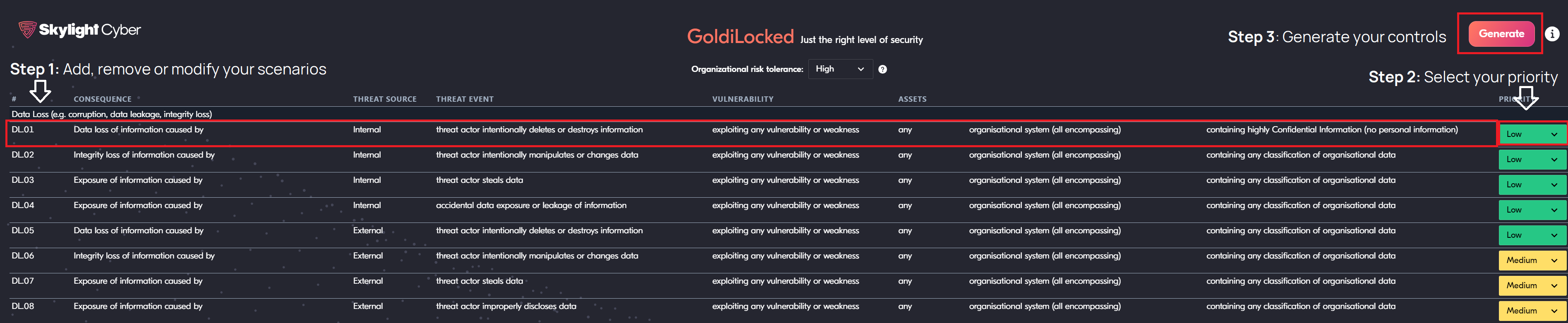
You can use Goldilocked using 3 easy steps, shown below.
GoldiLocked includes a set of basic risk scenarios that we think could be a good fit for many organisations. As a first step, you can review these scenarios and add, modify or remove the scenarios to fit your own organisation.
Once you have your basic set of scenarios, you can further tailor them by setting your priority (high priority represents low risk tolerance) for each scenario which influences the controls that would be recommended to reduce the risk within appetite. Selecting a high priority will result in more controls being suggested whereas lower priority will result in less controls.
Our tool combines popular control frameworks and standards, such as CIS Controls, NIST CSF v1.1 and ISO and maps them to the relevant risk scenarios.
Once satisfied with the scenarios, you can hit the “Generate” button to output a spreadsheet containing the list of tailored controls that map to each risk scenario.
GoldiLocked can be accessed here: https://goldilocked.skylightcyber.com/
Limitations of the tool
While this tool assists in taking the first step in applying a risk-based approach to security, we recommend that it is used as a starting point on your security journey. The controls might need further tuning and potentially additional guidance in terms of level of implementation maturity.
Give us feedback
It is worth mentioning that this is a first iteration of the tool and we understand there might still be some kinks to work out. We are happy to receive your feedback and ideas on how to make GoldiLocked more useful at [email protected]